Operations | Monitoring | ITSM | DevOps | Cloud
SIEM
The Fatal Unconnectedness of Incumbents from Customers: The Tale of a Race Against the Clock
This tale is based on an actual event that happened to one of our Cribl Search customers. It highlights a massive gap between the urgent needs of modern businesses and the outdated, draconian terms dictated by traditional SIEM vendors. While the events are real, a touch of dramatization was added for the fun of it. Why not?
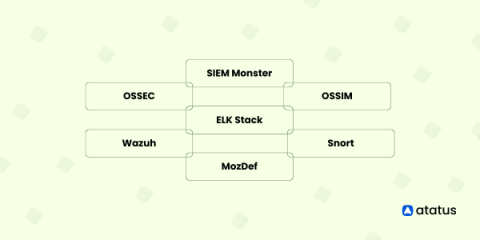
Top Open Source SIEM Tools
In the fast-paced world of cyber security, organizations face a challenging task to safeguard their digital assets from a variety of advanced threats. Security Information and Event Management (SIEM) tools have emerged as a vital solution, empowering businesses to detect, respond to, and mitigate security incidents effectively.
Why Cyber Resilience Is Foundational to Your SIEM Success
The common failure scenarios that occur in the cybersecurity world are typically assumed to be costs of doing business, but they’re actually more predictable and avoidable than you might imagine. Even if you’ve been lucky enough to avoid failed data sources or backups, a SIEM getting knocked offline, and other cybersecurity attack situations until now — in today’s day and age, they’re still inevitable.
SOAR vs. SIEM: Understanding the Differences
This post was written by Joe Cozzupoli. Scroll down to read the author’s bio. As the cybersecurity landscape evolves and threats become more sophisticated, organizations need to stay ahead with the right tools and strategies to protect their valuable data. Two key technologies in this domain are Security Orchestration, Automation, and Response (SOAR) and Security Information and Event Management (SIEM).
Logz.io Cloud SIEM Available on AWS AppFabric at Launch
Logz.io is honored to have our Cloud SIEM as one of the products available as part of the launch of AWS AppFabric. For customers invested in AWS, this inclusion allows you to use our cloud-based, agile SIEM seamlessly alongside other critical SaaS applications.
Accelerate Investigations, Forensics and Audits Using Cribl Search and Amazon S3
In the era of big data, data lakes have emerged as a popular way to store and process massive amounts of data. Fortunately, with Cribl Search and Cribl Stream, you can create a Data Loop to optimize the use of your data lake by saving Search results as part of an investigation. Our four-part video series explains how to set up Cribl Search and Cribl Stream to establish a Data Loop using the Amazon S3 Data Lake destination in Cribl Stream and the Cribl Stream in_cribl_http source.
3 Keys to Maximizing SIEM Value
SIEM has been a crucial component of security systems for nearly two decades. While there’s ample information on operating SIEM solutions out there, guidance on evaluating and managing them effectively is lacking. We’ve noticed many SIEM vendors are taking advantage of this dearth of knowledge and not providing customers with needed value for what they’re buying.
Modernize Your SIEM Architecture
Top 3 SIEM Optimizations - How to Get More From Your Existing Tech Stack
In today’s digital-first world, most security problems are actually data problems, and data volumes are outpacing organizations’ abilities to handle, process, and get value from it. You’ll have 250% more data in five years than you have today, but the chances of your budget increasing to match that are slim. The challenges that come with managing the rise in enterprise data volume directly affect your ability to adequately address cybersecurity risks.