Operations | Monitoring | ITSM | DevOps | Cloud
Vulnerability
How Implementing Risk-Based Patch Management Prioritizes Active Exploits
Resistance to change is always present, especially if you think the processes you have in place are efficient and effective. Many organizations feel this way about their software management procedures until they have a security breach or incident and are left wondering where they went wrong. The reality is that most patch management programs are built on assumptions and recommendations, rather than facts about actively exploited vulnerabilities. Risk-based patch management is the answer to this issue.
What is so Pro in Ubuntu Pro?
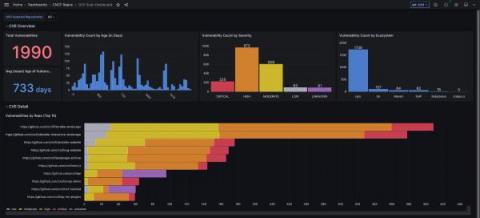
How to manage CVE security vulnerabilities with Grafana, MergeStat, and OSV-Scanner
Patrick DeVivo is a software engineer and founder of MergeStat, an open source project that makes it possible to query the contents, history, and metadata of source code with SQL. The security posture of software supply chains has been a significant topic lately. Recent high-profile breaches have shown the importance of managing risks from third party code. Take, for example, the Log4Shell vulnerability (tracked as CVE-2021-44228 — Grafana Labs was not affected).
A comprehensive review of the best vulnerability scanning tools
In this article, we explore the features and capabilities of the top five vulnerability scanning tools so that you can consider all the key factors before selecting one.
Securing Kubernetes at KubeCon: Vulnerabilities, Supply Chain, and Policies
New Chrome and Edge zero-day exploits: How to patch CVE-2023-2033 and CVE-2023-2136
Patch Windows Common Log File System Driver Vulnerability (CVE-2023-23376)
Outlook Zero-Day (CVE-2023-23397) Fix for N-central and N-sight
As you likely be all too aware, there is a Microsoft Outlook zero-day vulnerability listed under CVE-2023-23397. With the increased attacks on Outlook this month, Microsoft has pushed out fixes for about 80 Windows flaws. More information on some of those patches can be found in my colleague Lewis Pope’s March 2023 Patch Tuesday blog. Lewis was also kind enough to send over the remediation script for both N-able N-central and N-able N-sight.
5 Advanced DevSecOps Techniques to Try in 2023
If you're here, you know the basic DevSecOps practices like incorporating proper encryption techniques and embracing the principle of least privilege. You may be entering the realm of advanced DevSecOps maturity, where you function as a highly efficient, collaborative team, with developers embracing secure coding and automated security testing best practices.