- April 2024 (3)
- March 2024 (3)
- February 2024 (2)
- January 2024 (2)
- December 2023 (4)
- November 2023 (9)
- October 2023 (8)
- September 2023 (5)
- August 2023 (6)
- July 2023 (21)
- June 2023 (6)
- May 2023 (8)
- April 2023 (7)
- March 2023 (20)
- February 2023 (3)
- January 2023 (5)
- December 2022 (5)
- November 2022 (4)
- October 2022 (3)
- September 2022 (2)
- August 2022 (4)
- July 2022 (1)
- June 2022 (2)
- May 2022 (1)
- April 2022 (1)
- March 2022 (1)
- February 2022 (2)
- January 2022 (1)
- November 2021 (1)
- September 2021 (4)
- August 2021 (5)
- July 2021 (4)
- June 2021 (2)
- May 2021 (4)
- April 2021 (4)
- March 2021 (7)
- February 2021 (5)
- January 2021 (3)
- August 2020 (1)
- July 2020 (5)
- April 2020 (2)
- February 2020 (3)
- December 2019 (1)
- November 2019 (1)
- October 2019 (2)
- September 2019 (1)
- August 2019 (4)
- July 2019 (2)
- June 2019 (1)
- March 2019 (1)
- February 2019 (7)
- November 2018 (1)
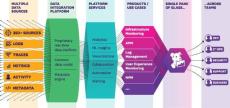
ChaosSearch makes it simple for organizations to run cloud-scale log analytics in their own Amazon S3 cloud storage. It uniquely transforms your cheap, secure, and durable cloud object storage into a distributed analytic data lake where scale is infinite, cost is disruptive, and access is universal.
Traditional log analytics weren’t designed for today’s tsunamis of log data. They require brute force (adding more and more compute) to search and analyze huge stores of logs. This means businesses must continually choose between spending more money or reducing data retention.
ChaosSearch’s SaaS data platform was built for a data-entrenched world. It’s based on the company’s patent-pending index technology and architecture that remove the limits, cost, and complexity inherent in conventional solutions.
- Performance at Scale: Easily scales to petabytes and beyond so you can analyze what you need, whenever you need.
- Fully Managed Service: There’s no software or hardware for you to deploy, configure or maintain.
- All on Your Amazon S3: ChaosSearch stores and analyzes data directly in your own Amazon S3 cloud object storage. It does not hold or store any data.
- Disruptive Pricing: Costs up to 80% less than other solutions, thanks to Chaos Index’s unique properties that eliminate the need to manually shard data and enable unparalleled compression ratios.