From PowerShell to p@W3RH311 - Detecting and Preventing PowerShell Attacks
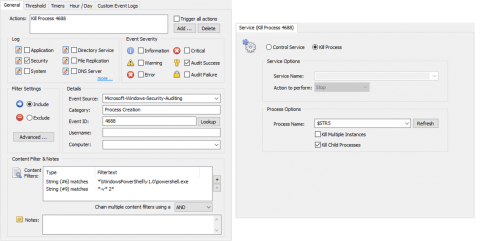
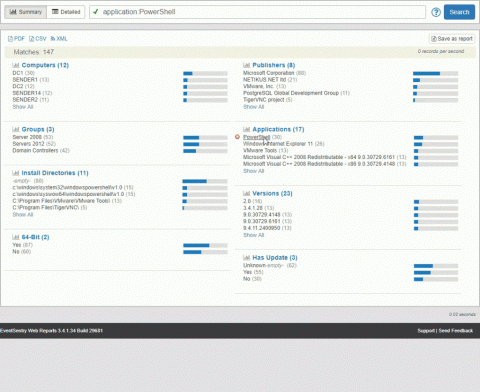
In part one I provided a high level overview of PowerShell and the potential risk it poses to networks. Of course we can only mitigate some PowerShell attacks if we have a trace, so going forward I am assuming that you followed part 1 of this series and enabled: Module Logging, Script Block Logging, Security Process Tracking (4688/4689)